In recent years, virtual machines have come to the aid of data centers. With virtualization, you can build systems with different workloads on the physical infrastructure and quickly move one virtual machine from one server to another without interrupting its service. You increase productivity. You save the status of a virtual machine to quickly restore the virtual machine if it crashes. These are a limited number of the benefits of virtualization.
Today, the use of virtualization in the data center is inevitable. Because of its widespread acceptance and usefulness, the concept of SDN or software-defined networks was created. VMware redefined all the boundaries of virtualization with its product, NSX, and introduced the concept of true large-scale SDN to everyone. Software-Defined Networks are a new type of network management system that divides the network into two levels of management level and data transmission level. In these types of networks, the management level is responsible for the control and planning for implementation at the sending level. The forwarding plane, also called Forwarding Plane, is responsible for directing traffic to the destination. SDN gives you a centralized view of the network. One of the most popular protocols used in software-based networks is the OpenFlow protocol.
NFV (Network Functions Virtualization) is also a new area in the network that can be implemented virtual and software network elements. Elements are hardware devices that are implemented separately; devices such as firewalls, routers, switches, load balancers, and the like. Obviously, buying and implementing any of this equipment is costly, time consuming and requires expert work. That's why NFV has come with the help of network administrators to reduce their costs and complexities. NFV complements software-based networks. Using these two technologies, VMware has launched a product called NSX. This product combines the benefits of both software-based and NFV network technologies.
In 2012, VMware acquired a company called Nicira, which worked on network virtualization and software-defined networks, and the project's birth goes back to that time.
The main task of NSX is to create and manage a virtual network. Just as using a virtualization platform can create, store, delete and retrieve a virtual machine, NSX can also create, store, delete, and retrieve a virtual network. The result is a highly flexible data center in communication that can, in the shortest amount of time, make different adjustments; delete a path, create a new path, create a backup link, and the like. With NSX, the current hardware is all you need to implement a software-defined data center.
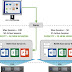
There are currently two different versions of NSX. The first version of NSX for vSphere is suitable for use with the vSphere environment. The second version is NSX for Multi-Hypervisor, which is suitable for cloud environments such as OpenStack. Figure 1 shows a comparison of the two network virtualization approaches and the virtualization platform for building a virtual machine. As shown on the left of this figure, in hardware virtualization, a hypervisor is installed on the hardware. In the upper layer, it is built into a software and logic virtual machine that exhibits the same hardware features and can easily be modified to the hardware specifications of a machine. On the right side of Figure 1 is shown how NSX works. The NSX includes a network virtualization platform that simulates the features of a network. Virtual networks are deployed on this platform and two-to-seven-layer services can be provided through these virtual networks. Services such as switching, routing, firewall, quality of service (QoS) and network load balancing.
Figure 1. Comparison of two different approaches to virtualization
NSX Components:
The NSX has four components. These components are shown in Figure 2, which include:
2. Management Plane
3. Control Plane
4. Date Plane
Figure 2. NSX components
1- Cloud Consumption:
The CMP (Cloud Management Platform) shown above is not, according to VMware, a core component, but because it can be integrated virtually with any CMP through the NSX REST APIs, it is one of the NSX components. They count. VMware claims through this layer's API that it is easy to create custom NSX modules for any cloud environment. NSX is now ready to integrate with VMware vCloud Automation Center, vCloud Director and OpenStack, the company said. The company has called this feature out-of-box integration. NSX can be integrated with OpenStock to connect to OpenStock via the Neutron plug-in.
2- Management Plane:
This section includes NSX Manager. The part where you can centralize the network. Most pundits consider this to be the same level of management in SDN as mentioned. With NSX Manager, "Single point of configuration" can be achieved. Figure 3 shows the NSX Manager console accessible through the browser.
Figure 3. NSX Manager console
The NSX Manager runs as a virtual machine in vCenter and requires installation and setup via OVF installation. According to VMware, there can only be one NSX Manager per vCenter. If you have multiple vCenters and communicate between them, you have created a Cross vCenter environment. Usually in such an environment there is a primary NSX Manager and several secondary NSX managers. In such an environment, there could be at most one NSX Manager and seven secondary numbers. The main task of the NSX Manager is to create rules for switches, routers and logical firewalls across the entire Cross vCenter environment. The secondary task is also to manage the network services locally and specifically for each vCenter.
3- Control Plane:
The Control Plane also consists of the NSX Controller Cluster. As the name of this controller is known, it is a The Control Plane also consists of the NSX Controller Cluster. As the name of this controller is known, it is a does not pass any traffic and its crash does not affect the Data Plane and the traffic flow. NSX Controller sends network information to hosts. The information that is sent to other parts of the NSX Controller is very important because if the information is sent incorrectly, the network settings will crash and the entire network will crash. For this reason, the likelihood of failure must be reduced. VMware has used the simplest way to increase redundancy to solve this problem. In this way, instead of implementing one NSX Controller, three NSX Controllers should be implemented and voted between commands. If the command or command gets at least two votes, it will execute, thus crashing a specified NSX Controller and preventing the execution of incorrect commands. If the two NSX Controllers are used, if the answers are different, the correct answer cannot be identified and a "Split-Brain scenario" problem arises. By implementing this cluster, which contains three controllers, you will also achieve High Availability. For information on the techniques of increasing redundancy and familiarity with its methods, see Barry W.Johnson's Design and Analysis of Fault-Tolerant Digital Systems. In each cluster, there is one node as the main NSX Controller. If a major NSX Controller fails, another node in the corresponding cluster is selected and known as the original NSX Controller. Other nodes in the cluster need to be in sync with them and synchronization is constantly happening.
4- Data Plane:
The Data Plane includes the NSX vSwitch which works with the vSphere Distributed Switch (VDS). The kernel NSX modules, user space agent, configuration files, and installation scripts are included in the VIBs and, after installation, run with the vSphere kernel to enable services such as distributed routing, logical firewall and VXLAN bridging. Figure 4 is an image of the vSphere web client after installing NSX. After installation, an icon named Networking and Security will be added to the Inventory section. After clicking on this icon, you will be redirected to the NSX homepage.
Figure 4. Added new item in vSphere Inventory
VIB, abbreviated as vSphere Installation Bundle, functions almost like ZIP files, except that this is the format for vSphere. VXLAN stands for Virtual Extensible LAN. VXLAN is a network virtualization technology designed to solve problems that make the network scalable. VXLAN uses encapsulation techniques (such as VLAN) to encapsulate two OSI layer-based Ethernet frames into four UDP layer packets.
Some of the benefits of using NSX vSwitch are as follows:
• Facilitate the implementation of many virtual machines
• Features such as Port Mirroring, NetFlow/IPFIX, LACP, backup and restore entire network settings, network health check, quality of service (QoS), efficient and very useful tools for traffic management and monitoring and ultimately network troubleshooting.
Talking about this software is not limited to these topics and the issues are so large and complex that various books have been written to explain them. That is why we intend to provide a simpler explanation with a simple and practical example.
A simple scenario:
One of the features of the NSX is the firewall. The equipment in this scenario and its network communications are shown in Figure 6. There are two Cisco 2960 ToR switches in the rack, two Cisco X4748 switches in the Aggregation layer, two hardware firewalls, several servers and two virtual machines. (ToR) stands for (Top of Rack) or (Top Rack).
Figure 6. Equipment available before NSX implementation
Network engineers intend to limit layer 3 traffic through the firewall. In this case, the following will happen:
2. The firewall may create a bottleneck.
3. As the size of the network grows, you need to buy more firewall devices, which increases hardware costs (Capex costs).
4. All firewalls can be accessed if the firewall penetrates.
5. This type of structure consumes a lot of bandwidth and will reduce network performance. For case number five, consider Figure 7. In this figure, the virtual machine number 1, which is marked in green, has an IP address of 10.1.0.5/24 and intends to associate it with the virtual machine of number two, which is purple in color and has an IP address of 10.2.0.8/24. To communicate with virtual machine # 2, virtual machine traffic 1 must pass through the (ToR) switches and pass the Cisco X4748 switch to reach the firewall. Upon reaching the firewall, the incoming traffic is checked and determined to be unauthorized and the traffic being blocked is blocked.
Figure 7. To check traffic, you have to go a long way
Some network equipment manufacturers have developed products that monitor traffic from one virtual machine to another and shorten the path that this traffic takes to be monitored, but there is still the problem of bandwidth loss. The NSX has a Distributed Firewall (DFW) feature that is a distributed firewall. This feature is activated when installing the NSX Manager vCenter plugin. One of the main benefits of this feature is that the firewall is brought to the virtual machine level; This means that any packet that exits or wishes to enter the DFW checks on or after DFW entry. According to Figure 8, the difference between this structure and the traditional structure is that DFW knows the virtual machine is not the number one allowed in the machine. Virtual sends traffic number two, so it checks the traffic when it leaves the virtual machine and is denied access to the network platform.
Figure 8. Traffic check after leaving virtual machine
If you move your virtual machine from server to server, the network structure on the new server may be different and your traffic will not pass through the hardware firewall for review or may require new modifications to your hardware firewall. Now, with the NSX DFW, all the rules and policies that you define for a virtual machine's traffic are moved from one part to another with the virtual machine and do not follow the physical structure of your network.
Finally
VMware, which has many virtualization products, has also been able to help improve the efficiency and functionality of the data center with a new hypervisor that virtualizes the network. NSX is a prime example of a combination of software-based networks and NFV. With NSX you can achieve SDDC (Software Defined Data Center) and reduce your fixed and even variable costs. Talking about this very interesting and useful software does not end there. All of the above is a prelude to this software and a careful examination of its structure and capabilities is beyond the scope of this article. At first glance, this software is very useful, but there are still questions in our mind that need to be further researched on how it works. First, no matter how virtual the network is, it will definitely need to pass through the physical infrastructure traffic. Now, what are the arrangements to avoid the traffic load on a physical link? Can this software detect the physical link load? How does one find the nearest logical route to an address and take physical characteristics into account? Questions such as these may be of great importance to you. So, we suggest learning more about NSX implementation and considering the physical conditions of your network.
https://drive.google.com/file/d/19sMW0aYe77rrq7mV92diadpz2NyPowOD/view
Abd El-Rahman Oreiby
Senior Data Center Engineer
Al Thuraya Security Egypt
www.abdelrahmanoreiby.weebly.com
VMware NSX New Virtualization Boundary
 Reviewed by Abd El-Rahman Oreiby
on
6/22/2020 08:40:00 م
Rating:
Reviewed by Abd El-Rahman Oreiby
on
6/22/2020 08:40:00 م
Rating:
 Reviewed by Abd El-Rahman Oreiby
on
6/22/2020 08:40:00 م
Rating:
Reviewed by Abd El-Rahman Oreiby
on
6/22/2020 08:40:00 م
Rating:







ليست هناك تعليقات: